Scaling development teams with Cloud Workstations
I've been wanting to try out Cloud Workstations for quite a while, and finally got the chance to set it up and had a good play around with the setup process and the capabilities it enables.
If you prefer to see a full walk through of Cloud Workstations in a video, click here
What is Cloud Workstations
Cloud Workstation serves as a platform that enables development teams to conduct secure software development activities in a cloud-based environment, with Google Cloud Platform (GCP) being our chosen cloud provider. Its value becomes particularly evident when managing the scalability of expansive remote teams, ensuring the availability of reproducible environments, and mitigating risks or accessibility issues associated with local development setups when accessing cloud-based services.
Imagine yourself as a developer in a typical setup, where the platform team establishes a foundational blueprint known as the Workstation Configuration. This configuration dictates the software components installed within it. As a developer, you interact with a Workstation created based on this predefined configuration. Depending on your setup, you have two options:
- You can opt for a browser-based development environment, which means you can comfortably work even with a less powerful laptop. Yes, you can achieve everything you need within your web browser.
- Alternatively, you can choose to develop locally using tools like PyCharm Pro, but here's the twist: all your code execution occurs within the Workstation instance, providing a seamless integration between your local development environment and the cloud-based Workstation.
Key Benefits
Cloud Workstations provides the following key benefits
- Reproducible dev environment, this is particular useful for a large group of people, especially remote workforce
- Get around laptop issues which often has a lot of restrictions to install software
- Improved security, you can control from images used to if internet access is allowed
- Testing your code with real services running in the cloud (i.e. private cloud run endpoint, private IPs within your VPC network)
And it is particularly powerful in a large business where there are a lot of remote workforce needing a consistent software development setup with better control
How to it up
The setup procedure is relatively uncomplicated. Simply navigate to the specific section of my video where I have provided a detailed walkthrough of the Workstation Configuration setup, as this is the only step that demands a little extra effort on your part.
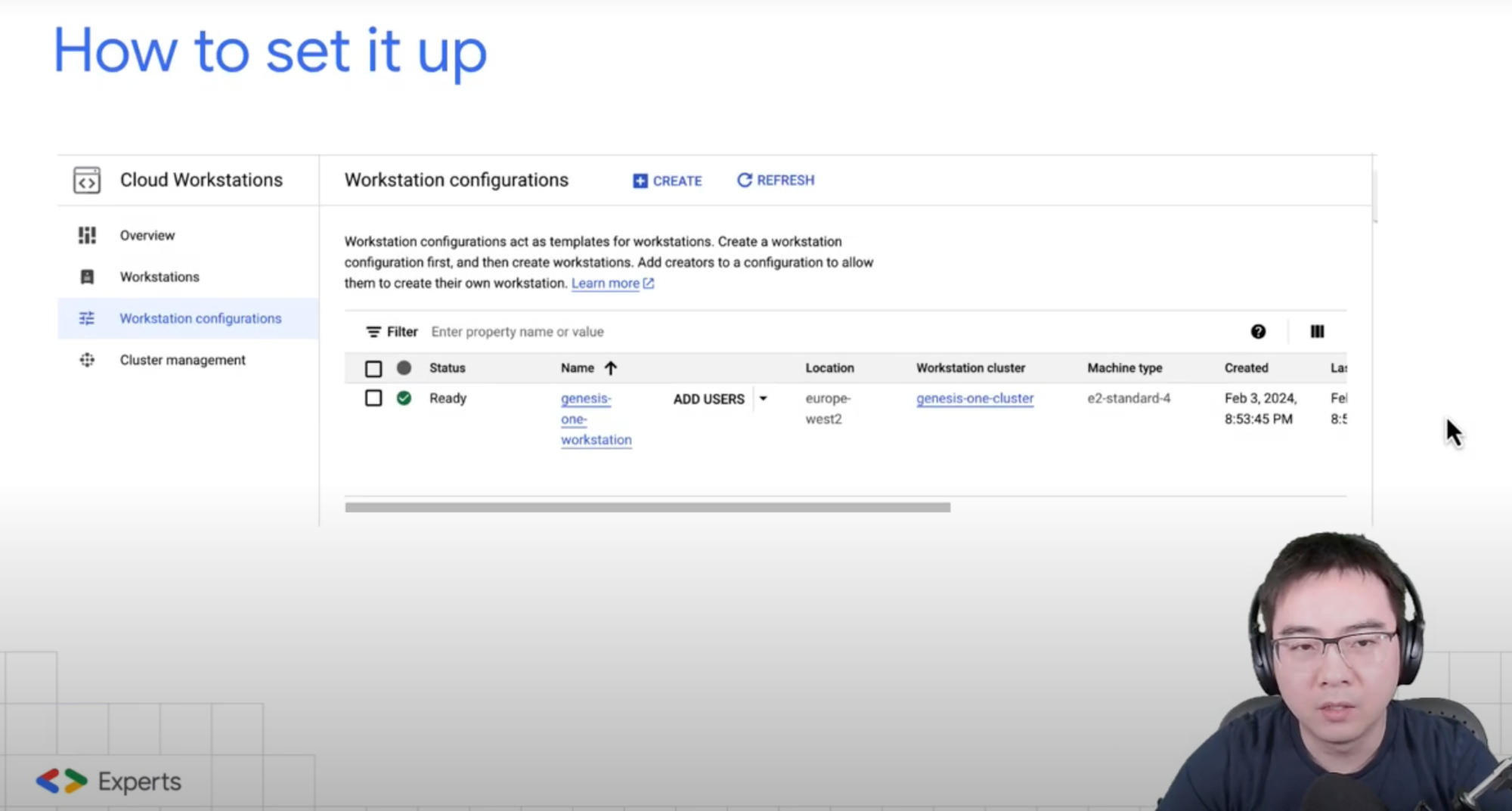
There are a few key points I would like to mention here though,
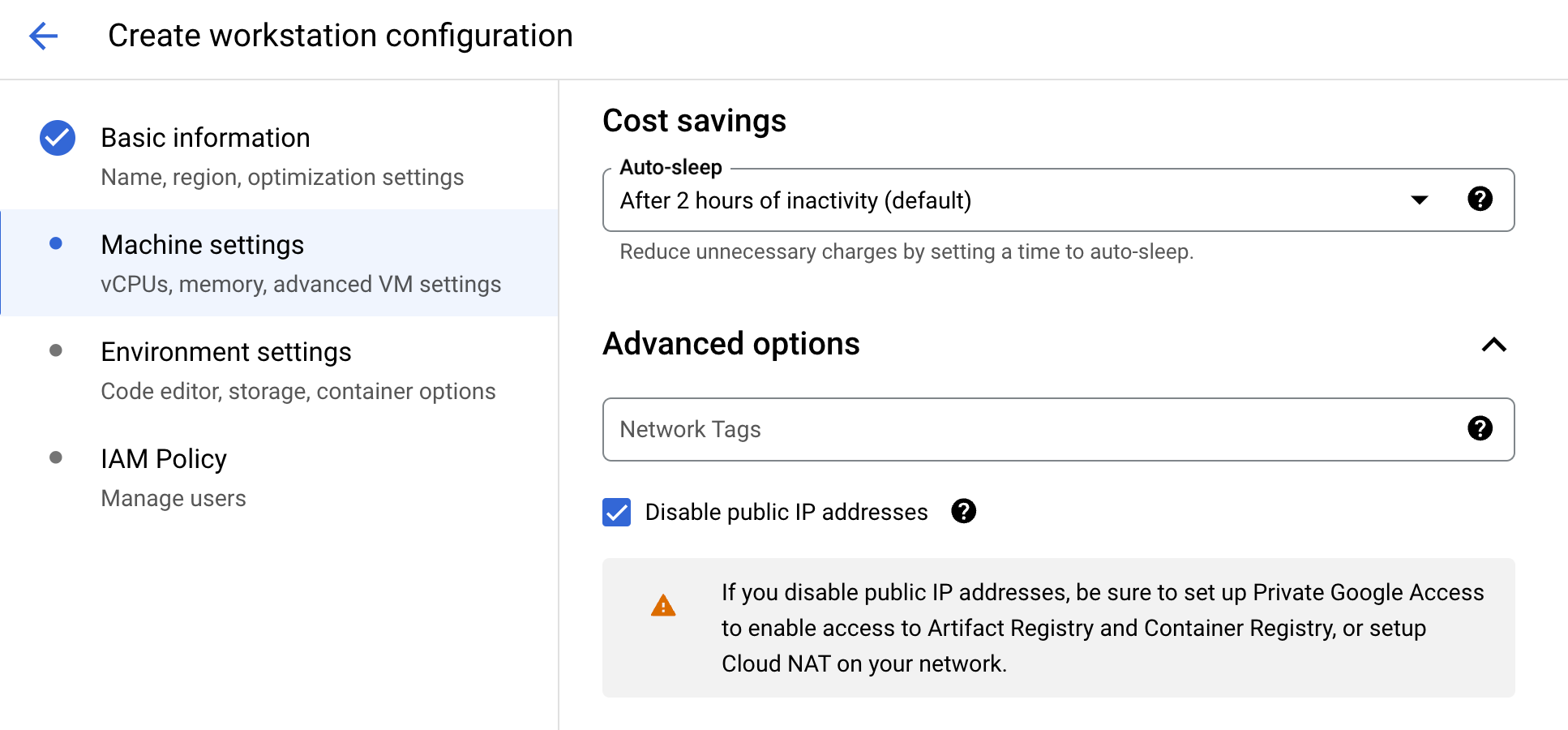
When setting up machines, Public IPs should be disabled, and if access to the internet is required, use Cloud Nat instead.
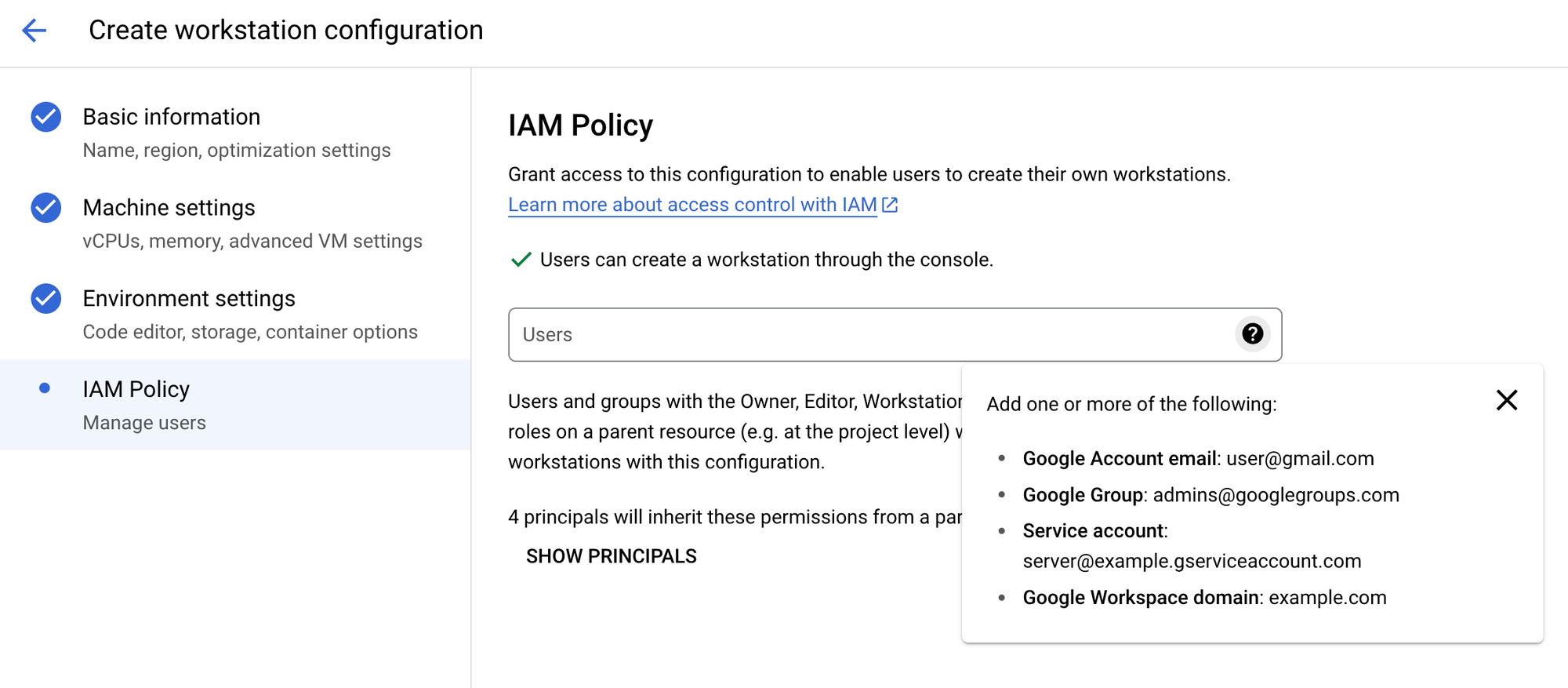
You can delegate the ability to create Workstations to more groups. This can be very handle if you train a group of admins who then takes on the responsibility to manage Workstations for their own teams
Demo and useful tips
If you're interested in witnessing a demonstration along with some valuable insights, you'll find a dedicated section in the video below that offers a comprehensive overview of the Browser IDE.

And it's more than just an IDE for coding, it also provides you with a fully operational terminal complete with persistent disks.
Summary
To sum it up, Cloud Workstation provides straightforward setup, a satisfactory browser-based development environment, the capacity to test code with actual services within a VPC network. However, it entails a time-consuming workstation configuration process lasting approximately 30 minutes and lacks support for community version IDEs such as PyCharm CE.

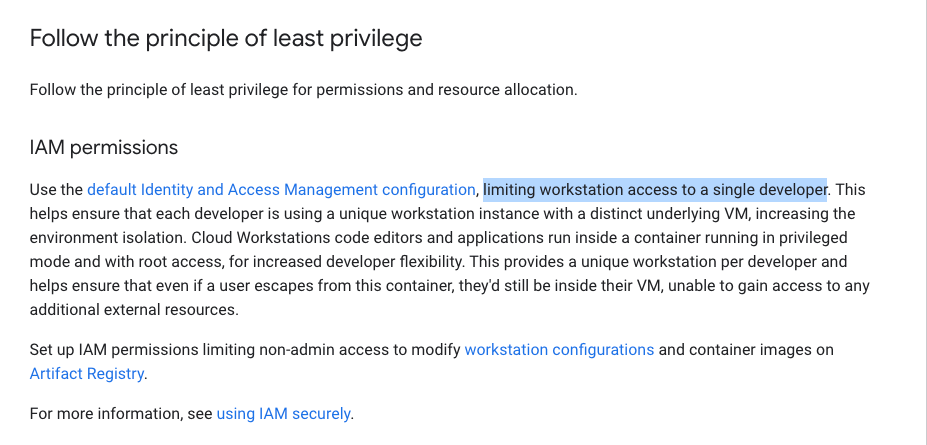
Another crucial point worth highlighting is the need for caution when granting access to a single workstation among multiple individuals. Best practices strongly recommend a one-developer-to-one-workstation setup, a strategy that aligns with logical reasoning. Nevertheless, it is noteworthy that the configuration allows for the effortless assignment of a group of users to a single workstation, which may prove advantageous on certain occasions but often raises more security concerns than it resolves. This is because the token generated by one developer can be accessed without explicit authorisation, potentially posing significant security risks.
Comments ()